Sophisticated and integrated security solutions

According to Cybersecurity Ventures, the cost of cybercrime is predicted to hit $8 trillion in 2023 and will grow to $10.5 trillion by 2025.
Unmatched security
Lightstream can assist you with security assessments, enabling you to gain a comprehensive understanding of your current security posture, including strengths, weaknesses, and vulnerabilities. We’ve got the expertise to help you thorough evaluations of security controls, policies, and procedures in place, assessing the effectiveness of existing security measures. We can also help you employ various methodologies, such as penetration testing, vulnerability assessments, and risk assessments, to identify potential weaknesses and vulnerabilities in the infrastructure. We’ll help you uncover hidden security gaps, prioritize security investments, and develop targeted strategies to mitigate risks and strengthen your overall security posture.
IT professionals everywhere are moving to a Zero Trust Network Access (ZTNA) architecture. ZTNA is a security framework that enforces strict access controls, treating all network traffic as untrusted, regardless of its source or location. ZTNA verifies and validates the identity, device health, and context of users and devices attempting to access resources. It dynamically grants access based on policies that consider various factors, such as user authentication, device security posture, and real-time risk assessment. We can help you adopt a Zero Trust model, to enhance your security posture, minimize potential attack vectors, and protect critical resources from unauthorized access.
Need help managing and monitoring your cloud and IT infrastructures? Lightstreams offers a blend of XDR, MDR, and traditional endpoint detection and response (EDR) services tailored to your distinct needs. Our 24/7 monitoring extends to IT infrastructure, endpoints, firewalls, cloud environments, and beyond. With a dedicated team of security experts, we not only detect threats in real-time but also respond with precision across various vectors. Utilizing advanced tools in our Security & Network Operations Centers, we promptly identify and address any suspicious activity or vulnerabilities. By partnering with LightStream’s, you’re ensured robust protection for your vital assets and an effective mitigation of risks. Enjoy peace of mind, letting us handle your security while you concentrate on your core business. operations.
We are dedicated to helping you protect your end users, regardless of their remote location or the devices they use. We understand the challenges posed by a dispersed workforce and the need for robust security measures. With our advanced endpoint protection tools and 24/7 monitoring, we fortify your defense against threats attempting to infiltrate your IT infrastructure. Our comprehensive solutions include the latest endpoint detection and response (EDR) technologies with threat intelligence, behavior analysis, and real-time monitoring and remediation capabilities. We proactively detect and block malicious activities, ensuring that your end users’ devices remain secure and your IT environment remains protected.
Lightstream is your trusted partner when it comes to implementing next-generation firewalls (NGFW) and Firewall-as-a-Service (FWaaS) solutions. We understand the importance of a robust firewall system in securing your network infrastructure. Whether you prefer an on-premises NGFW deployment, a cloud-based FWaaS model, or a hybrid system that combines both, we have the expertise to design and implement the right solution for your organization. Our team works closely with you to assess your specific requirements, design a tailored firewall architecture, and seamlessly integrate it into your existing infrastructure. With Lightstream’s NGFW and FWaaS offerings, you can confidently defend your network against evolving threats, enforce access controls, and ensure the confidentiality, integrity, and availability of your critical resources.
As the popularity of the Secure Access Service Edge (SASE) continues to rise, you’ll need a trusted guide to help you design, implement, and manage your next-generation network that employs a SASE architectures. We understand the evolving landscape of network security and the need for secure and agile connectivity. We work closely with you to assess your organization’s requirements, design a tailored network architecture, and seamlessly integrate SD-WAN and SASE. With our deep knowledge of industry-leading solutions, we help you optimize network performance, enhance security, and simplify management across distributed locations. Our comprehensive services cover the entire lifecycle, from planning and network deployment to ongoing monitoring and support. You can confidently embrace the benefits of your SASE-based SD-WAN, leveraging agility, scalability, and robust security to achieve a secure and efficient network infrastructure.
Meet Lightstream Connect™

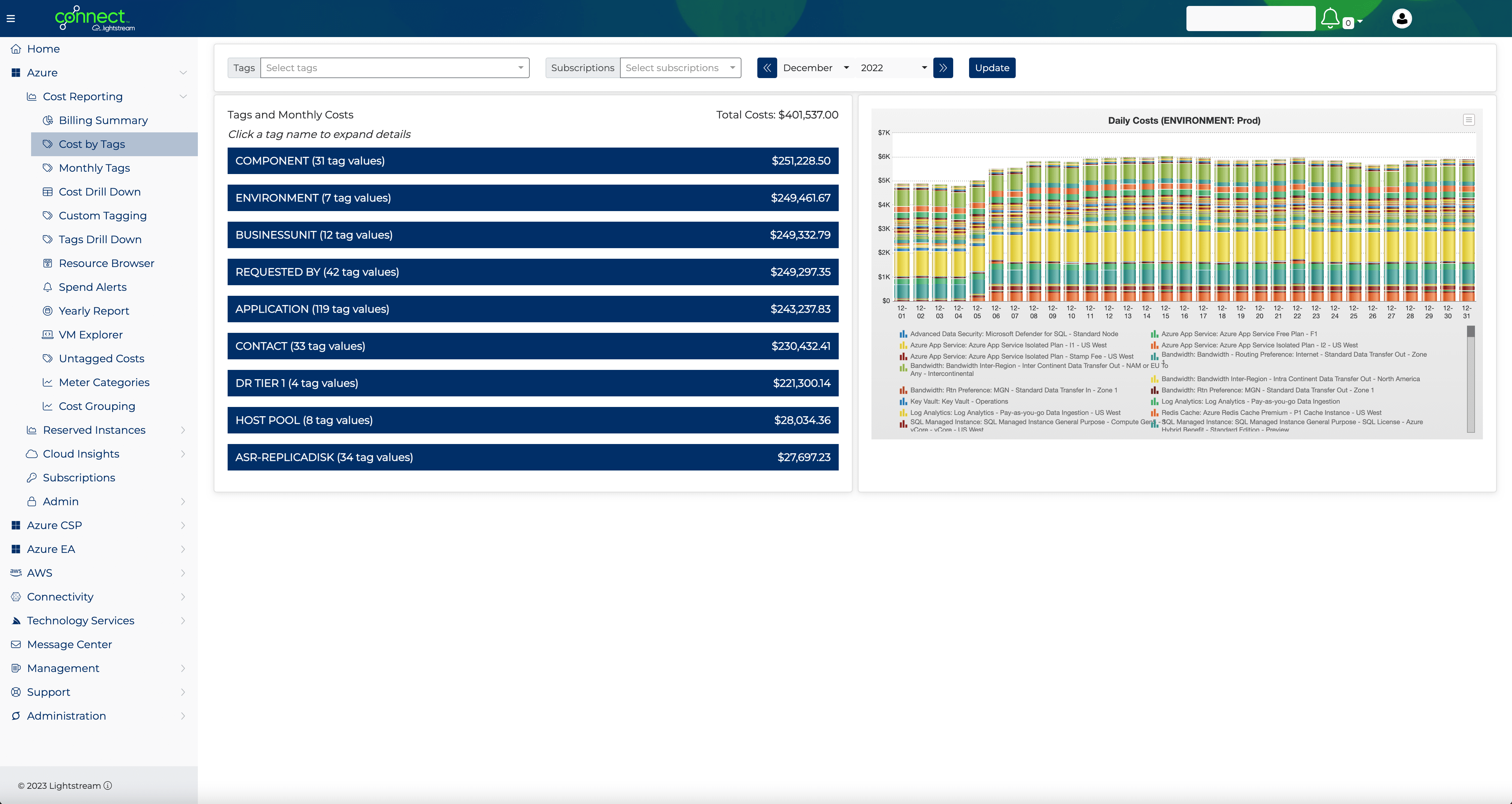
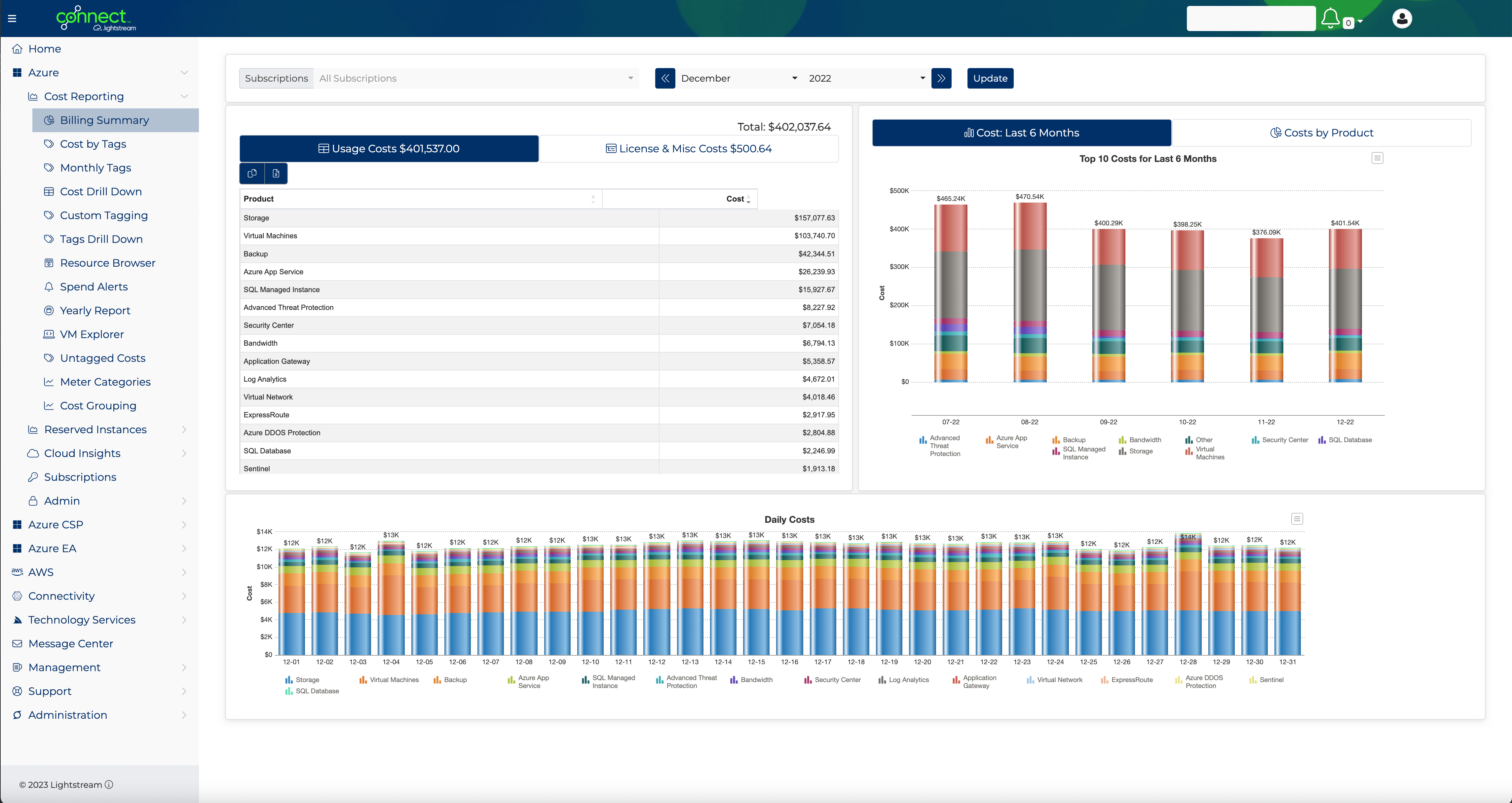
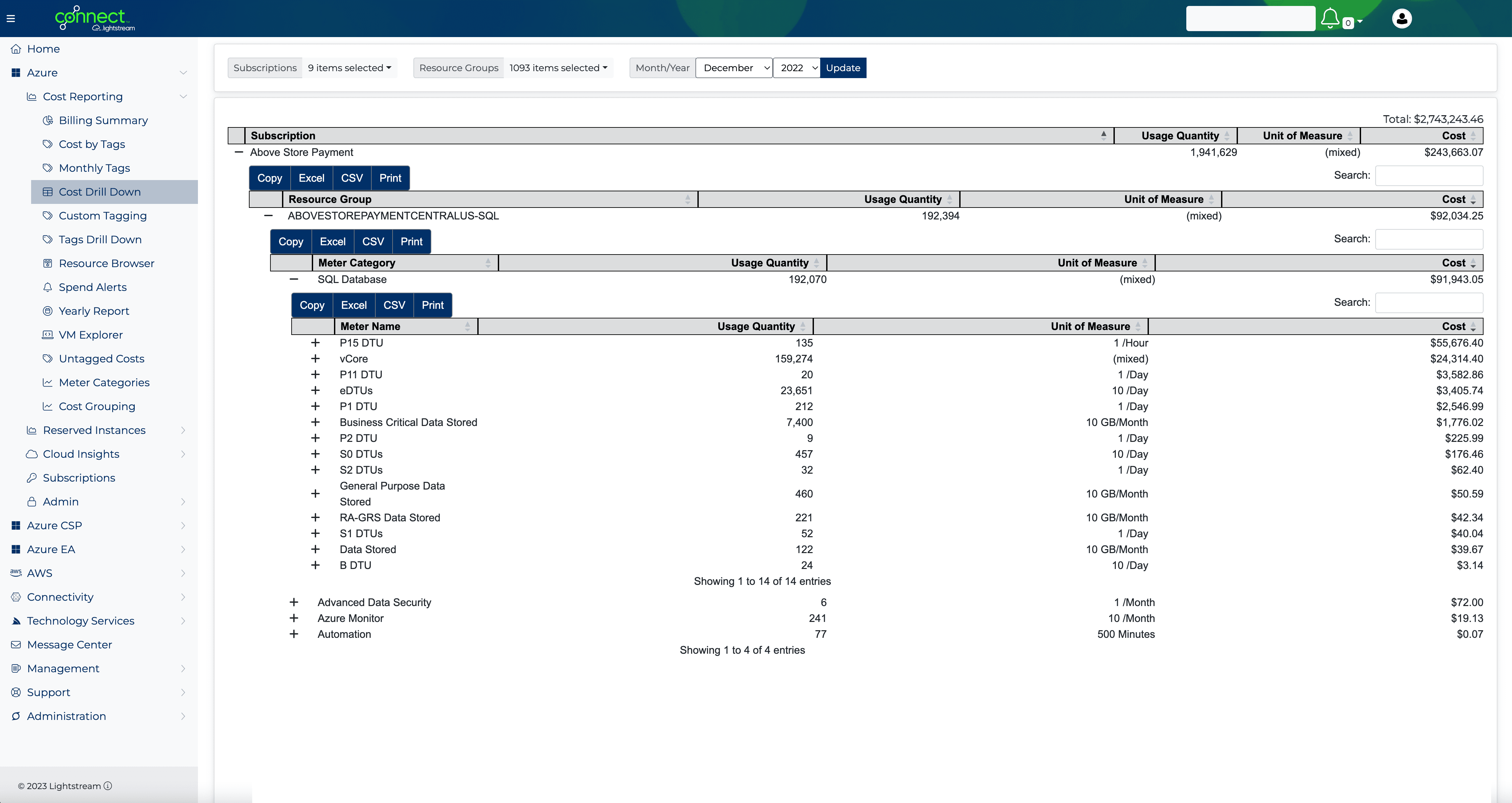
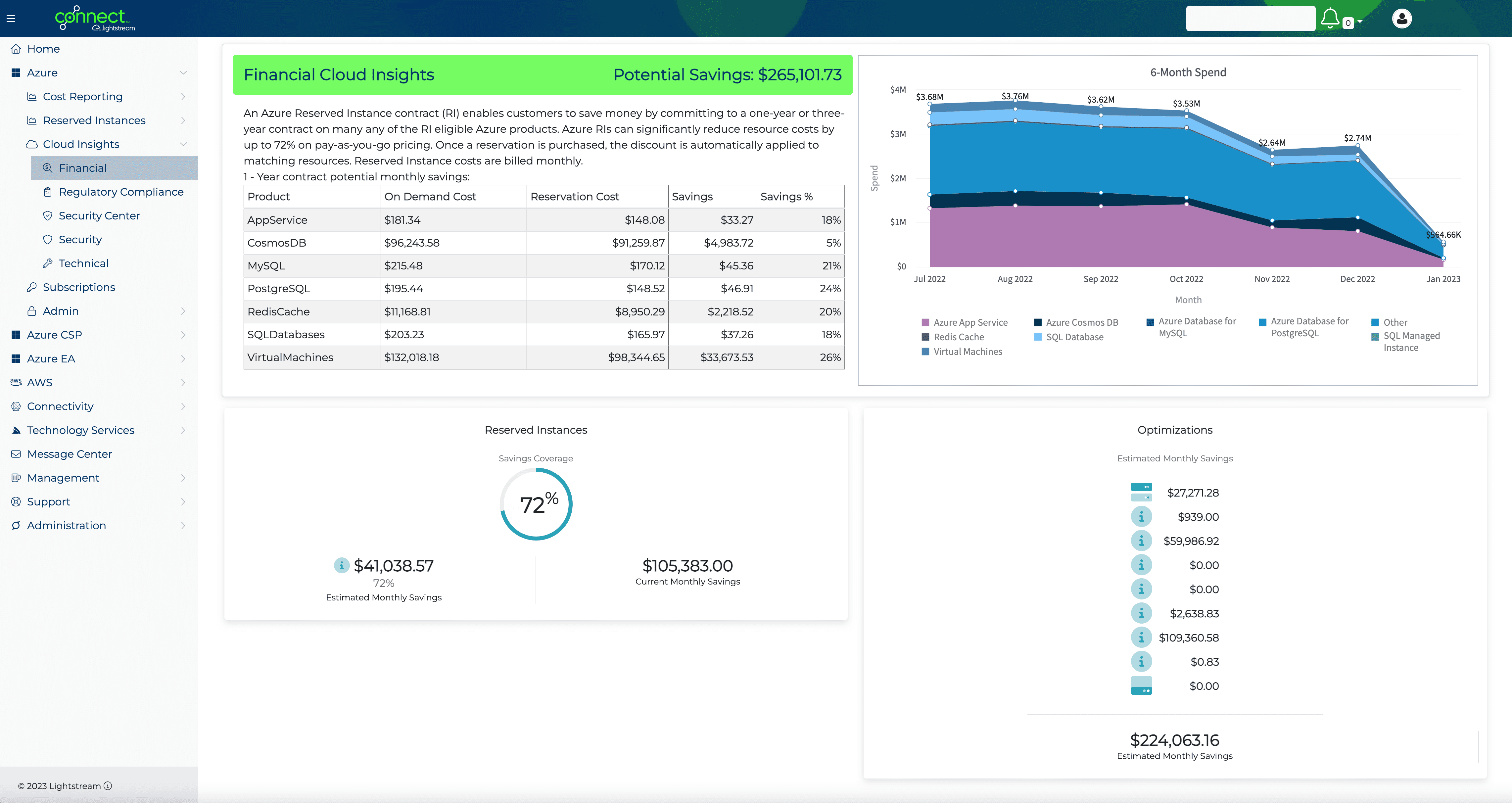
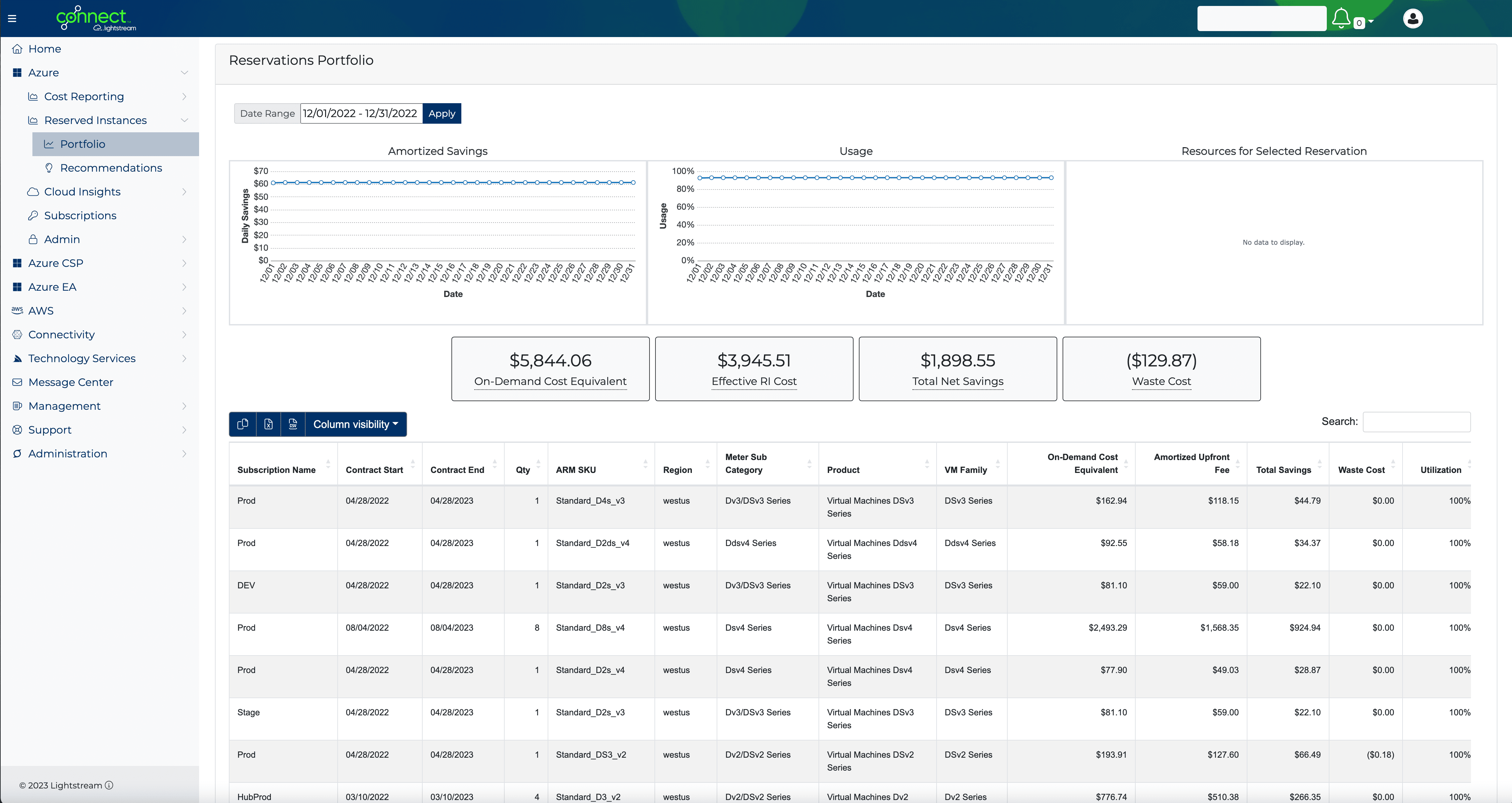
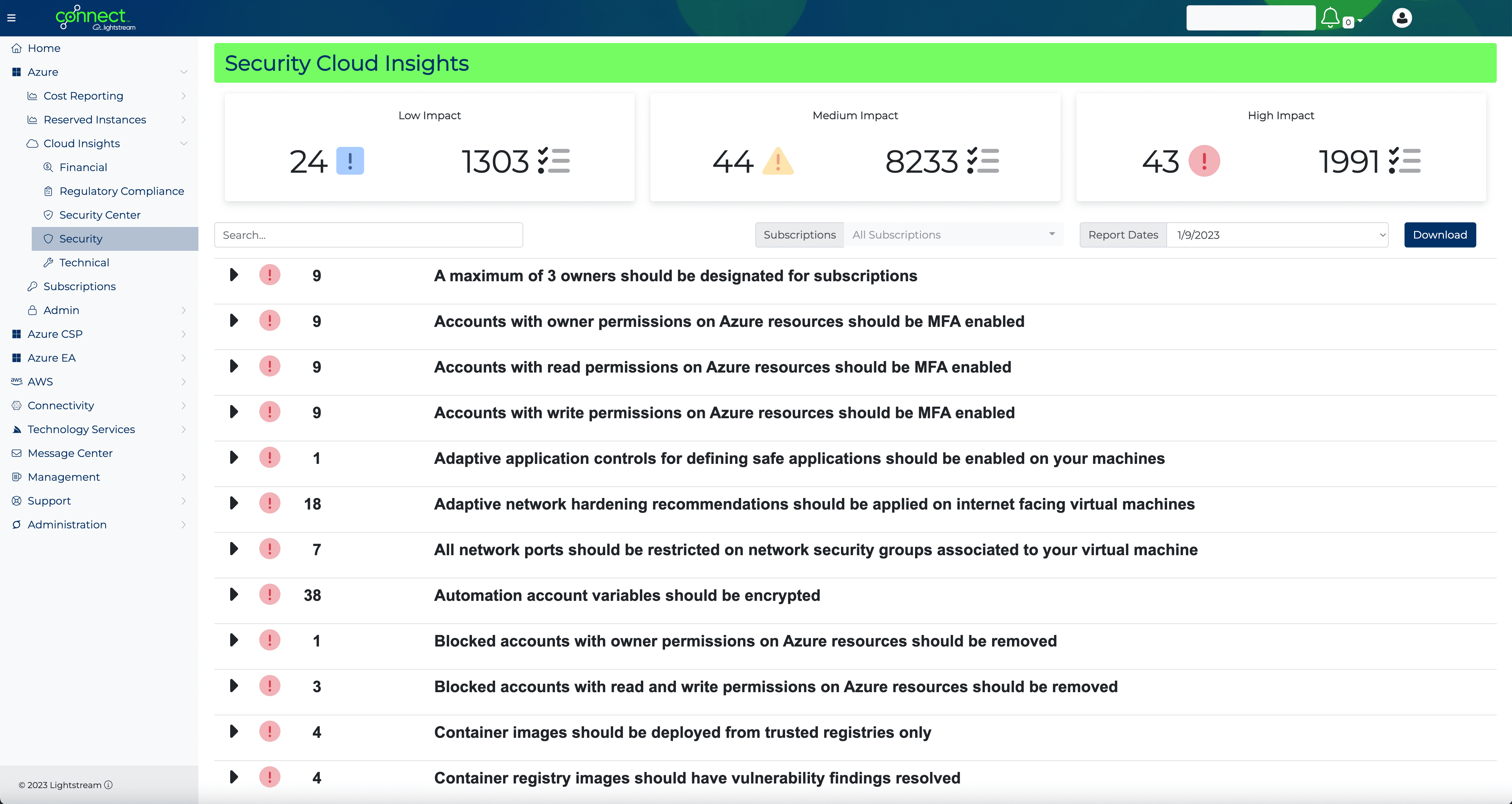
From retail and manufacturing to fintech and cloud, our dedicated solutions teams consulting-led approach to implementing best-fit solutions for your organizational needs without sacrificing quality, vision, or time to market.
Register for Lightstream Insights
©2025 Lightstream Managed Services, LLC. All Rights Reserved.